Owners and lovers of devices running the Android operating system will regularly tell you that one of the shortcomings of iOS is the fact that the visuals of the software can’t really be customized in any way. While this may be true for stock installations of Apple’s mobile operating system, performing a jailbreak on the device leaves the whole system open to intense customization.
Some jailbreakers prefer to go down the route of installing full home screen themes that involves pretty much every aspect of the user-interface being aesthetically changed, as well as individual system sounds being added and amended. One of the main benefits of that is; it makes your iOS device completely unique.
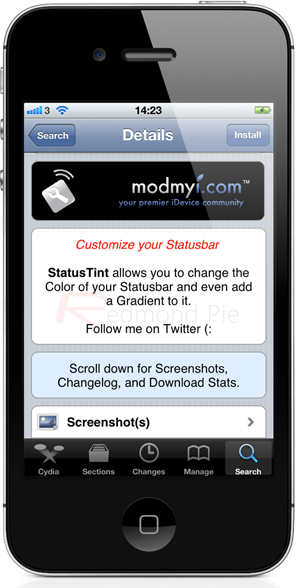
Some users prefer a more subtle approach to customization, something which the StatusTint tweak may provide. The StatusTint package is available from the jailbroken Cydia store and allows modification of the system-wide status bar that appears at the top of the operating system containing things like the signal strength indicator, the current time and battery level, as well as any data or Wi-Fi icons.
There are a number of reasons why an individual may want to amend the look and feel of the status bar, ranging from changing it to your favorite color or altering it so that it suits the aesthetics of your favorite or most used apps. Regardless of the reason, if you can look past the fact that it isn’t one of the most earth shattering packages in terms of functionality, it actually is a fun and relatively useful tweak.
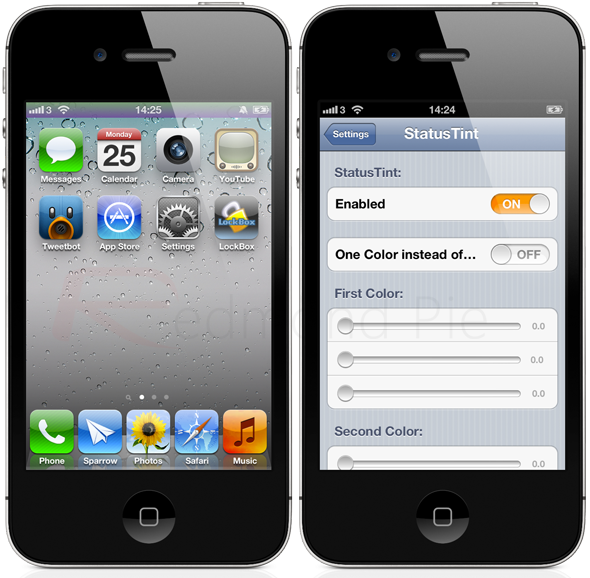
No additional home screen icons are added with StatusTint, with all of the modifications being possible through a dedicated preferences section in the Settings app. The required color can be set and amended using the supplied RGB sliders, with users also being given the option of setting the status bar to a solid color or mashing their own gradient pattern through the use of two colors.
StatusTint is available as a free of charge download from the ModMyi repository with no specific iOS version requirements being given.
Be sure to check out our iPhone Apps Gallery and iPad Apps Gallery to explore more apps for your iPhone, iPad and iPod touch.
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the web.
 Subscribe to our RSS Feed !
Subscribe to our RSS Feed !
Powered By WizardRSS.com | Full Text RSS Feed | Amazon Plugin Wordpress | Android Forums | Wordpress Tutorials


 With the year drawn to a mid, the tech industry has had its share of highs and lows. Whether it was the ensuing patent war, workforce taking the employers to court on grounds of anti-trust activities, a go-live of IPv6 or the CISPA coming into effect, it would probably be quite fair to assume that the industry has been in the sight of the regulators more than innovators.  Google’s controversial privacy policy changes, as exposed by SafeGov.org fit the discussion best.
With the year drawn to a mid, the tech industry has had its share of highs and lows. Whether it was the ensuing patent war, workforce taking the employers to court on grounds of anti-trust activities, a go-live of IPv6 or the CISPA coming into effect, it would probably be quite fair to assume that the industry has been in the sight of the regulators more than innovators.  Google’s controversial privacy policy changes, as exposed by SafeGov.org fit the discussion best.








 Sparrow for iPhone, formerly just a Mac OS X app, was launched a few months ago as a Gmail client. Recently, version 1.6 of the desktop app was released with support for POP accounts which meant that Hotmail and the likes would work with Sparrow. The same feature has just been added to the iPhone app as well so the list of compatible email services now looks something like below:
Sparrow for iPhone, formerly just a Mac OS X app, was launched a few months ago as a Gmail client. Recently, version 1.6 of the desktop app was released with support for POP accounts which meant that Hotmail and the likes would work with Sparrow. The same feature has just been added to the iPhone app as well so the list of compatible email services now looks something like below: (For PCWorld Pakistan)
(For PCWorld Pakistan)








